Our team was recently engaged to perform Incident Response and Digital Forensics services for a victim of LockBit ransomware. During the course of the investigation, the below artifacts were discovered.
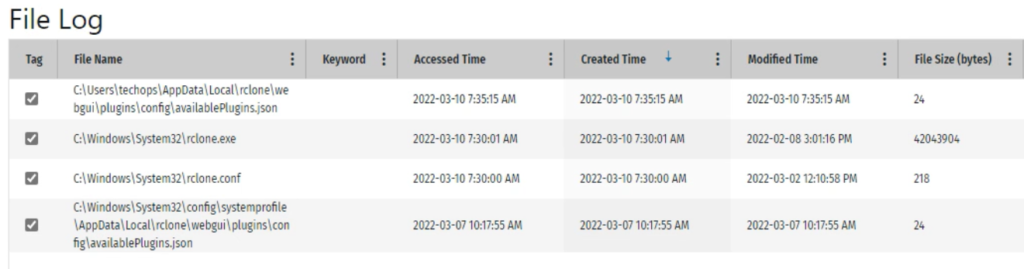
Discovering RClone indicated that it was likely data was exfiltrated from the environment. The critical focus then became as to whether it could be determined what data was exfiltrated. Examining the evidence a bit further, “rclone.conf” became of specific interest and focus. The contents (crypt passwords modified in screenshot to not expose exact credentials) are displayed below. This information helps to give insight into identifying the Threat Actors, along with showing they utilize the online storage repository MEGASync.
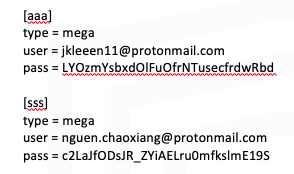
Research was performed to determine how a conf file is created. Utilizing this information, along with a separate user account created for testing, it was learned that a conf file could be moved from one computer to another, allowing access to the storage repository. Further research showed that the listed crypt passwords could be de-obfuscated to show the true credentials. This means with access to a conf file, full account access to the contained MEGA accounts is also possible.
Based on above research, it was possible to go back into the environment and perform further investigation into how rclone was utilized by the Threat Actor. This led to discovery of multiple victims. The victims were split into different MEGA accounts by month with “jkleeen11” being February and “nguen.chaoxiang” being March. (Victim names cut out of below screenshot for privacy purposes)
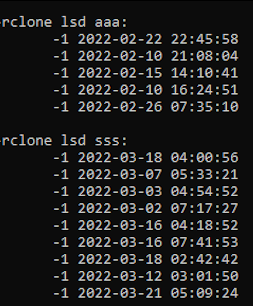
Rclone also gives other capabilities to interact with the data, such as, copy, sync, purge, etc. Thus, with access to a conf file, it would be possible to determine exactly what a Threat Actor exfiltrated from the environment, obtain a non-encrypted copy of the data (exfiltration occurs before Ransomware), and destroy it from the repository.
Analysis could also be performed to see if there was any correlation between exfiltrated data and posting of said data on LockBit’s website.

Finally, with research and a config file, would any additional identifying information about the Threat Actors be recoverable?
Fortunately MEGA also maintains / follows a “Privacy and Data Policy“. From it, of specific interest was:
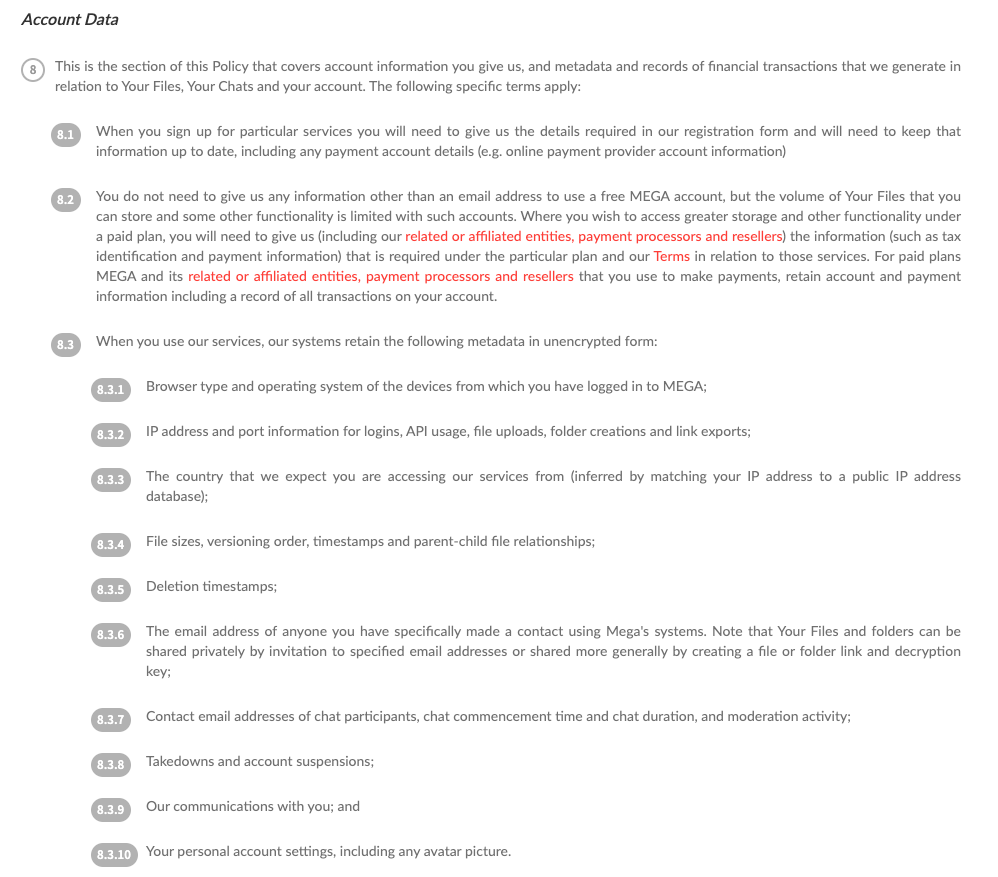
Thus, one can “Download your personal data” to receive a metadata report.
From said metadata report, a number of artifacts would contain relevant information; such as account holders, how payments were made, and finally, session IP Address details.