All tested ArubaOS / HPE switches are vulnerable to a Log Poisoning / Code Injection / XSS / Authentication Bypass flaw due to lack of proper input sanitization via the embedded SSH server. (Proof of Concept for YC.16.11.0003, Multiple Firmware & Devices)
The switches are part of a broader family of vulnerable network infrastructure devices modified or rebranded by multiple manufacturers. This family of products has been exploited multiple times by the CYBIR security team. The devices are also vulnerable to a Denial of Service (DoS) attack currently undisclosed.
In this disclosure, the switches are vulnerable to a remote, unauthenticated log poisoning and code injection (HTML/XSS/other) attack. Seen here, the security team injects valid HTML / XSS payloads into the LOGIN name field via SSH. The switch and operating system do not sanitize or control this input:
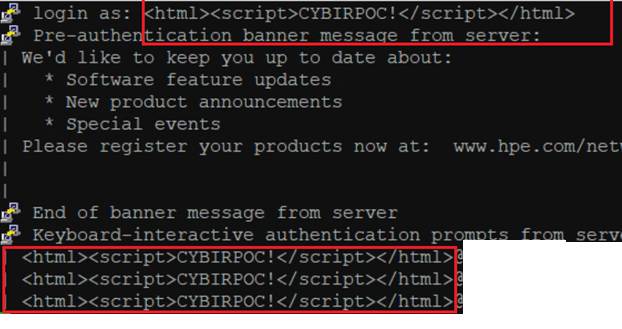
Using the available web interface and logging system, the security team requests the log file / entries from the device. The arbitrary HTML / XSS is injected into the log and is used to attack the authenticated user:
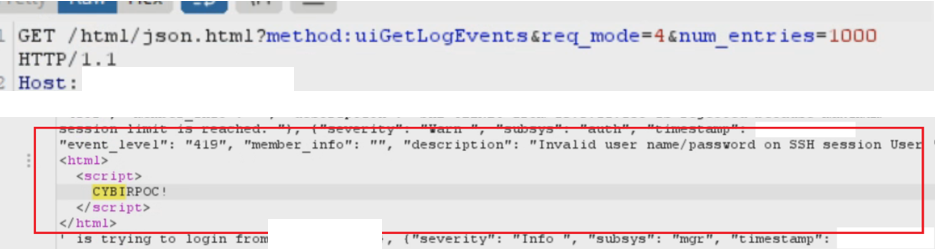
This can allow for theft of session / session riding, arbitrary code execution, and compromise of client-side browsers.
Other methods of XSS delivery and code injection were discovered by the security team and are currently being investigated. The details of this attack will be publicly shared due to criticality and research interest. When provided by Aruba, the patch for this exposure should be applied immediately.
The webserver on all affected devices should be disabled until a patch is issued.
PLEASE CREDIT KEN PYLE – PARTNER & EXPLOIT DEVELOPER, CYBIR