“The Gang Recycles Their Connectwise Trash Edition”
Answers: The recycling bin where you can pick them out and reuse them…. but their firewall and AV exceptions don’t go anywhere.
Part of the analysis Connectwise has used to dispute my research has leaned heavily on “Well, you’d need social engineering for that!”
https://www.connectwise.com/blog/managed-services/breaking-down-the-dangers-of-social-engineering
I found that answer a bit confusing given their published guidance for other businesses, specifically MSPs on the subject. They seem to think it’s a pretty significant vector of attack… but what if you didn’t need to trick anyone into clicking something? What if just drop-catching a name was enough?
https://en.wikipedia.org/wiki/Domain_drop_catching
Surely an elementary and simple attack like this is impossible and was considered….
Where do old Connectwise Control instances go when they die?
Security Trails is one of my favorite metadata aggregators and have been for a very long time. I’ve written for their blog, I’ve used their site for my research and talks. In fact, the one I authored last year is about to become very relevant again: (https://securitytrails.com/blog/blast-radius-exploiting-self-registration-services)
I’m a big fan of Security Trails’ many features.. but my favorite is the historic and current domain record collection:
https://securitytrails.com/list/apex_domain/screenconnect.com
Any malicious actor with a web browser now has the ability to search the history of SCREENCONNECT.COM. For instance, anyone can anonymously look for interesting domains and their history. Today, after a few seconds of scouring (No, I’m not malicious), I came upon some interesting ones. So I got curious. Has anyone ever thought of this and…..
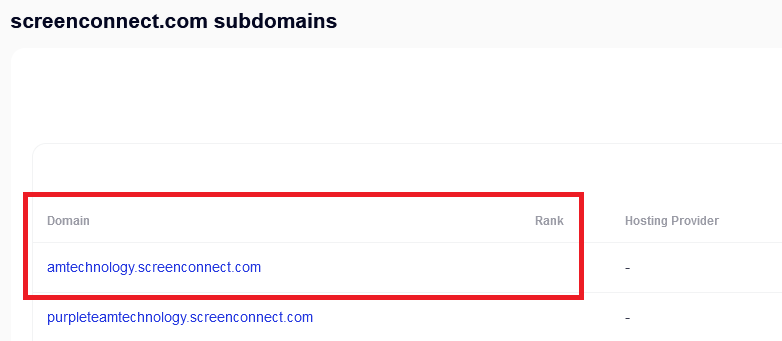
Why would anyone want to do that? Welllllllll…….
Digging Around In The Recycling Bin.
I was curious what happened to these old FQDNs and instances after the customer decided they were no longer using the product.
… because sometimes you need to fiddle with things to get them work…
… and manys time they’re never cleaned up. The new industry buzzword for this is “tech debt.” So I found a one of interest (seen above) and I registered this via a trial account with no validation:
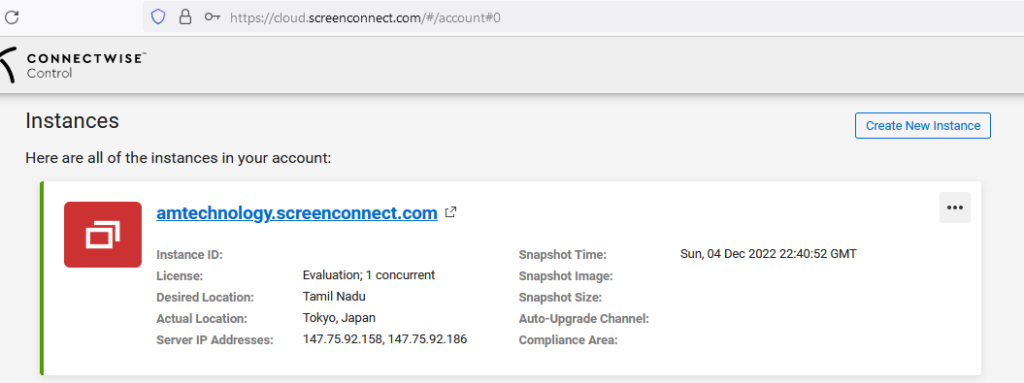
Remember, Connectwise is well aware of my concern of the ability to register instances AND domain names through several channels… including Brian Krebs. (https://krebsonsecurity.com/2022/12/connectwise-quietly-patches-flaw-that-helps-phishers/) I did this on DECEMBER 4th.
What I have now done is scooped up someone’s old instance name, exceptions, firewall rules, etc. Now all I have to do is wait on my watering hole for something to happen….
The Gang Recycles Their Trash
Wait…. what?
You see, Connectwise Control and Screenconnect are hybrid applications with changing parameters. These parameters and settings absolutely confound security controls or set off false alarms.
This software is very popular with administrators or MSPs who access sensitive endpoints at scale or have control & monitoring of extremely sensitive endpoints. Those endpoints *should* have fairly strict checking like Executable Signatures, SSL Certificates, and firewall or AV exceptions. What if you could recycle some old instance FQDNs and control or bypass all of these exceptions? You’d just need to know what FQDNs or Domains were whitelisted and acquire them:
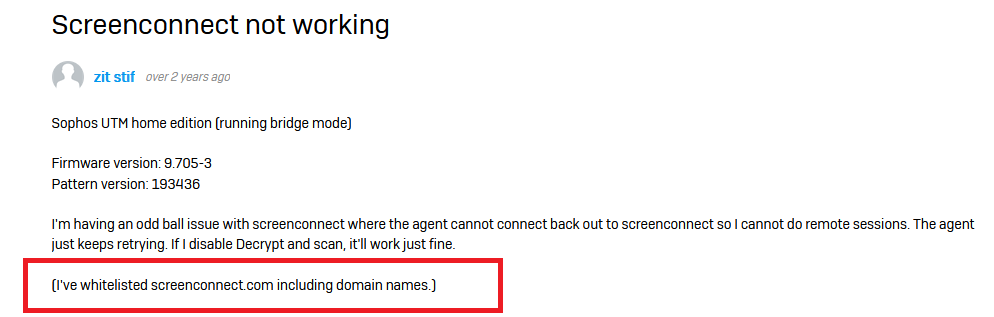
https://community.sophos.com/utm-firewall/f/general-discussion/124989/screenconnect-not-working
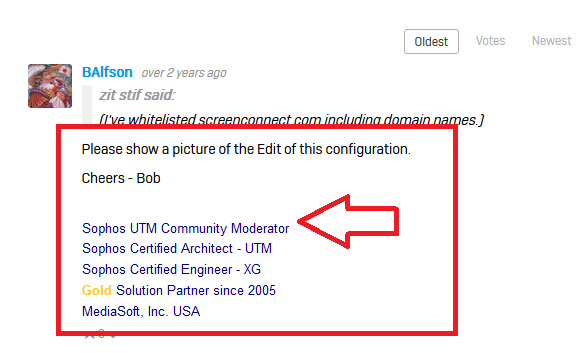
So I did. For free.
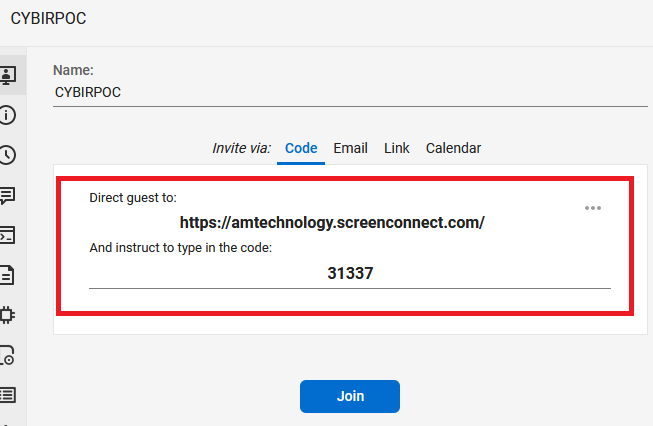
Now, what happens if SOMEONE or SOME ENDPOINT.. stumbles into my watering hole https://amtechnology.screenconnect.com/?
How bad is this? This behavior is not only abusable… it’s widespread!
Reddit, who has discussed my work already, has provided a lot of validation for my findings.
www.reddit.com/r/msp/comments/l2pu2e/connectwise_automate_whitelist_hosted_server_ips/
“We have had good luck whitelisting our FQDN for the hosted automate and control servers. Never needed to do the actual IP. We are a Sophos shop but I imagine most firewalls lets you define a host by FQDN instead of IP.”
Quite a lot do… and when all of those DNS records resolve to an untrusted zone… bad things can happen. All you need to do is find the right FQDN to scoop up.. or have someone tell you how to find it.… https://securitytrails.com/list/apex_domain/screenconnect.com
Don’t believe me about HOW BAD THIS PROBLEM IS?
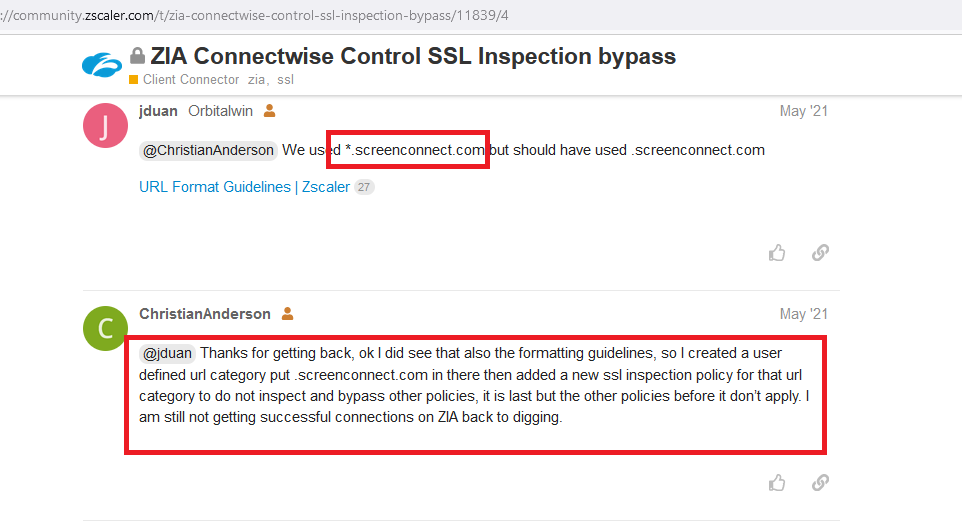
https://community.zscaler.com/t/zia-connectwise-control-ssl-inspection-bypass/11839/4
Ever look at the SSL cert used by *.screenconnect.com? Every instance, trial or not?
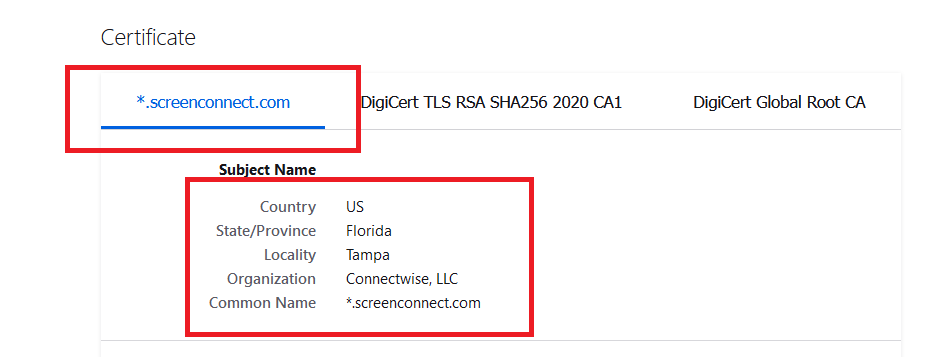
No social engineering needed.
“Domain drop catching, also known as domain sniping, is the practice of registering a domain name once registration has lapsed, immediately after expiry. ” What about subdomain drop catching Connectwise…. and all of it’s domain whitelisting or controls bypasses?

This analysis has some serious flaws and it is about a lot more than social engineering: www.reddit.com/r/msp/comments/yrkhs2/connectwise_control_possible_vulnerability/
More on this later… a LOT more.