In this release, we demonstrate a technique for farming Storage, Appliance, and IoT self-provisioning & dynamic registration services to build hyper accurate maps of internal networks, controls, and users.
Our PoC will demonstrate using DATTO dynamic DNS registrations to identify vulnerable hardware at the Department of Defense, Meraki metadata to identify users, firewalls, and vulnerable devices inside CISCO networks, GEOVISION devices to establish a complex botnet, and farm DNS registrations to identify key storage areas and vulnerable software.
Through refinement of the techniques provided, an attacker can use the caches and profile a single DNS zone, SSL CA, or HOST HEADER attack to perform reconaissance. Refining futher and collecting this metadata from multiple vendors services can allow for extremely accurate targeting, profiling, and exploitation of corporate & government networks at massive scale. (ex. Mirai.)
BLUEMONDAY and the series of works we are releasing are interwoven around a core set of fundamental design flaws that most experts and researchers have either unintentionally or, in some cases, outright ignored & intentionally built into their products. The CYBIR team has refined 0-day exploits and attacks against these appliances and documented findings. These will not be distributed publicly as part of this release. (We are not “those guys.” We are highly ethical. have an excellent reputation, and we care deeply about the security of EVERYONE.)
The focal point of THIS release is that this information is stored FOREVER in historical DNS caches, SHODAN, search engines, etc. The vendors may attempt to flush their networks, try to minimize the impact, or portray this in a negative light. There is quite simply no other solution to this problem than starting to work on it NOW and not in 6 months or a year when they quietly slip it under the radar. (More on this in a few weeks.)
Until then, an APT, criminal, or even a curious teenager can easily, quickly, indirectly (undetected) map out your internal / external network, firewall rules, authentication mechanisms, crawl massive appliance networks through these flaws and cause the next 20 type MIRAI botnet attacks to happen *with ease* all through third party services and historical metadata caches.
Overview
Vendors like DATTO, MERAKI, GEOVISION, SYNOLOGY, EGNYTE and others are which leverage or depend on these services are imperiling data, networks, and businesses through insecure design, intentional design decisions, and web application flaws.
These devices frequently self-provision services which leak critical data or through insecure network design and installation practices which are easily mapped, attacked, and discovered via insecure vendor, software, and integrator practices (ex. PKI, Dynamic DNS, “Finder” service registrations, DNS leakage, Layer 2 Attacks / DHCP network attacks, DNS passive hijacking through domain purchases & active record injection)
This release is an entry point into a larger family of vulnerabilities currently being studied by the researcher. The number of techniques, exploits, and 0-days outlined in this work are novel, previously undiscovered, or original concepts being actively pursued by the researcher. This document provides essential PoC for DNS, PKI, and third party service metadata leakage, farming, exploitation of devices and vendor networks, an example of passive DNS abuses, and novel & new methods of automatic code execution through fundamental flaws in web design and the affected products.
Some concepts and new attacks may be obliquely referenced or held private by the researcher. Essential PoC is contained in this document and is easily reproduced using supplied narrative and screenshots.
The affected devices are easily discoverable either through insecure practices (ex. insecure Zones, algorithmic FQDN generation, lack of local network controls, public metadata leakage) or vendor provided interfaces and access methods. (DATTOWEB, DATTOLOCAL, SYNOLOGY.ME, DYNAMIC-M, GVDIP.COM, EGNYTE-APPLIANCE.COM)
Many issues develop due to these problems. For example, nearly all of these devices and appliances provide easily discoverable portals / content / metadata with which to craft extremely convincing social engineering campaigns, even in the absence of technical exploit vectors.
Host Header Attacks & 302 redirects used in concert with malicious DNS records / spoofed or squatted domains can be abused in this manner. An attacker can identify the MERAKI device a victim uses through registration, abuse the API to obtain senstive metadata, and send the victim to a spoofed site or malicious content purported to be a Meraki Dashboard alert. An attacker can change the dynamic DNS record through a number of vectors (ex. Third party service attacks, local vectors) and effectively “hijack” the user or content being accessed.
Through our DNS harvesting and our undisclosed 0-days, we can establish a complex exploit network and botnet via poor vendor controls (ex. MIRAI) We can also hide exploit code in APIs, persist across multiple appliance types, and abuse multiple dynamic DNS networks.
The DNS zones we have provided are intentionally designed, demonstrably insecure, provide detailed information, and can be abused easily. Registrations can be abused for data exfiltration or beaconing over the vendor’s DNS network. These DYNAMIC DNS services allow for efficient, mass exploitation and recon. The poor controls and “spoofability” of these networks (will demonstrate at another time) allow an attacker to not only FIND vulnerable devices.. but automate mass exploitation via attacks such as those we provided or other common attacks.
There are other sections of this overall project / work that we will be releasing at a further date. We will be providing exotic / new exploits and attack techniques exposing potentially m/billions of endpoints and users.
Lastly, the researcher’s domain registrations and canaries for this work also served to prevent the attacks outlined here as well as the entire class of NAMEWRECK attacks from being triggered by a malicious attacker. The author wishes for this to be noted as responsible disclosure and ethical considerations for the attacks / exploits seriously impacted disclosure dates and continues to.
DATTO – DATTOLOCAL.NET & DATTOWEB.COM DYNAMIC DNS ZONES – MAPPING AND EXPLOITING AT SCALE
The DATTO product line utilizes a number of components, services, APIs, user agents, and other framework to provide backup, data protection, and cloud services to a wide spectrum of clients.
The CYBIR security team has previously been publicly acknowledged by DATTO and US-CERT as the discoverer of critical issues in the DATTO line of products.(CVE-2015-2081: Datto ALTO and SIRIS Devices Allow Remote Code Execution Via Unauthenticated Requests to PHP Scripts – CYBIR (dfdrconsulting.com)) The security team examined the DATTO suite and discovered several potentially critical issues with the product, design, and administration by DATTO.
Local Information Leakage – MAPPING AND EXPLOITING AT SCALE
The DATTO device automatically provisions and encrypts data on the device. Additionally, the device supports “find anywhere” functionality, enabling a user to install the device on a network with or without supporting DNS infrastructure or traditional IT assets in place. The user needs only to type in a DATTO generated Fully Qualified Domain Name (FQDN) and DNS will forward the user to the correct IP Address.
These “finder” services are also highly abuseable in novel ways. For future release.
As part of this process, the device itself registers itself with an external SSL Certificate Authority (CA), Let’s Encrypt (Let’s Encrypt – Free SSL/TLS Certificates). Let’s Encrypt offers free SSL certificates which are fully externally validated and compatible with most web browsers and applications.
Many appliance devices vulnerable to our methods leverage Let’s Encrypt for PKI. This exposes farmable metadata, abuseable vectors, and attack paths at multiple points. For an attacker, there are now two locations from which to scrape metadata. (PKI & DNS)
The FQDN / Domain used for the DATTO self-provisioning process is *.DATTOLOCAL.NET. Both a DNS record and SSL certificate are externally registered and retrieved by the device.

Using this technique and overlaying other dynamic DNS registrations, such as internally leaked IPv4 addresses, an attacker can precisely target sensitive data locations, such as backup & storage devices. An attacker who wishes to deploy ransomware or destroy backups in anticipation of such an attack can identify vulnerable devices, which potential security & data privacy controls are in place, and can abuse HHI/Insecure DNS regimes to perform client-side hijacking and exploitation.
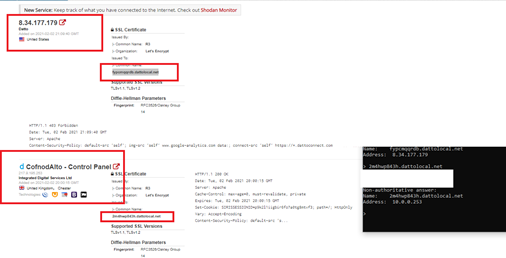
The security team demonstrates this issue via local DNS query. Seen here, the FQDN REDACTED.DATTOLOCAL.NET is applied to the SSL certificate and has registered itself via its local DNS server with an IPV4 private address.
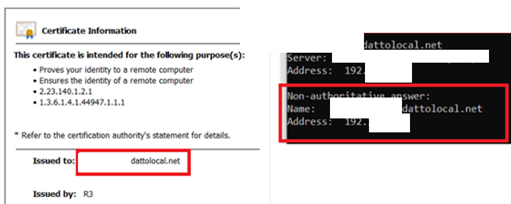
The security team queried this FQDN from an external IP address and network. Seen here, the security team queries the common well known resolver 4.2.2.2:
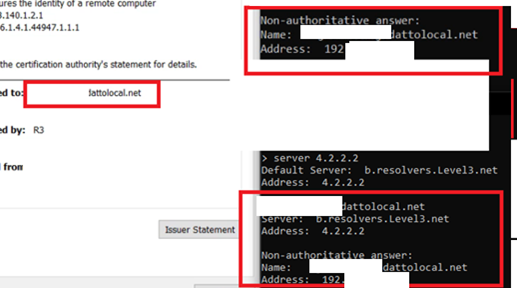
The DATTO device self-registers and dynamically updates external records based on this information. As seen above, critical information about the device’s environment (Internal IP Address) is not only exfiltrated to DATTO, it is discoverable publicly, passively, and with little technical effort. This zone fails to sanitize dynamic records and RFC1918 addresses. Due to this and it’s external service registration, an attacker has identified the internal IP of the target, that is is capable of reaching public addresses, and has registered on the Dynamic DNS host & beaconed it’s NAT/PAT RFC1918 address:
The attacker can accurate build firewall rule sets, trigger External DNS interaction to map egress points and trigger RCE or DNS based exploits, or stage massive DDoS attacks through a variety of techniques. We will not be disclosing our highly refined attacks and methods at this time due to other pending related releases and the resultant disclosure of additional new types of attacks & exposures.
Bulk DNS Metadata Collection & Metadata Analysis
Investigating these DNS leakage issues at scale through online repositories discloses private network metadata and information. Further, DATTO discloses an accurate estimate of the number of devices it has deployed globally through this oversight. (IN FACT, THEY ALL DID THIS!)
These packet captures, threat intel, and network metadata collections were scraped from a crafted “Google Dork” based on this FQDN for targeted information:
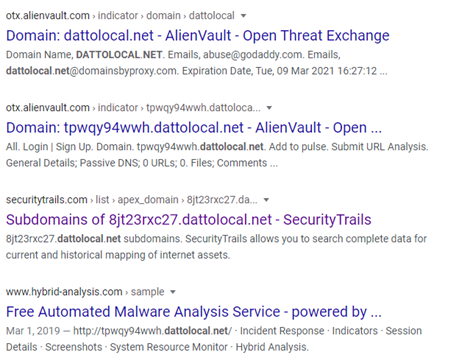
Note: Datto utilizes other DNS zones and registrations for their products, such as DATTOWEB.
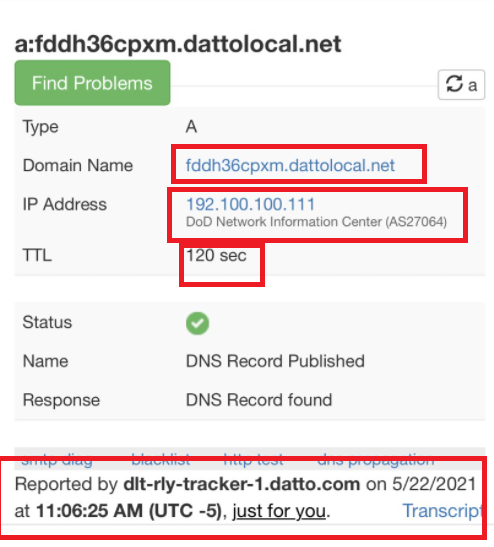
Finally, the security team identifies a DATTO backup device inside a Department of Defense network. The hostname and backup solution is leaked via third party registration. The short TTL and recent update indicate this device is online, reporting into the DATTO network, has direct internet access, and is potentially leaking sensitive metadata about the network it resides to DATTO:
MERAKI – DYNAMIC-M.COM DYNAMIC DNS ZONE – MAPPING AND EXPLOITING AT SCALE
The MERAKI product line utilizes a number of components, services, APIs, user agents, and other framework to provide network management, connectivity, and cloud management services to a wide spectrum of clients.
The security team has extensively examined the MERAKI suite and discovered several potentially critical issues with the product, design, and administration by MERAKI. The CYBIR security team has previously been publicly acknowledged as the discoverer of critical issues in the MERAKI line of products.(Information Paradox: “Above the Clouds” – Cisco Meraki AP as a Wireless WMD (and a heavy dose of industry criticism) – Part 1 (information-paradox.net))
Meraki devices offer self-registration and dynamically updates external records based on this information. Seen below critical information is discoverable publicly, passively, and with little technical effort. Passively scraping DNS records, it is possible to identify direct clients, installs, network infrastructure & security control maps, exact versions / login in portals / vulnerable infrastructure, etc:
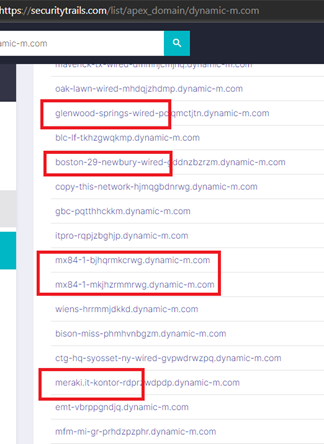
The API is well known and allows for aggressive farming of information and sensitive data (Cisco Meraki – Create with the Meraki Platform) Detailed platform information is easily gathered via API carving and anonymous web application browsing.
We again inspected the dynamic-m.com zone using similar techniques to our work against the datto. Doing so revealed an enormous cache of information, control maps, identifiers, and metadata.
One entry, however, was notable:
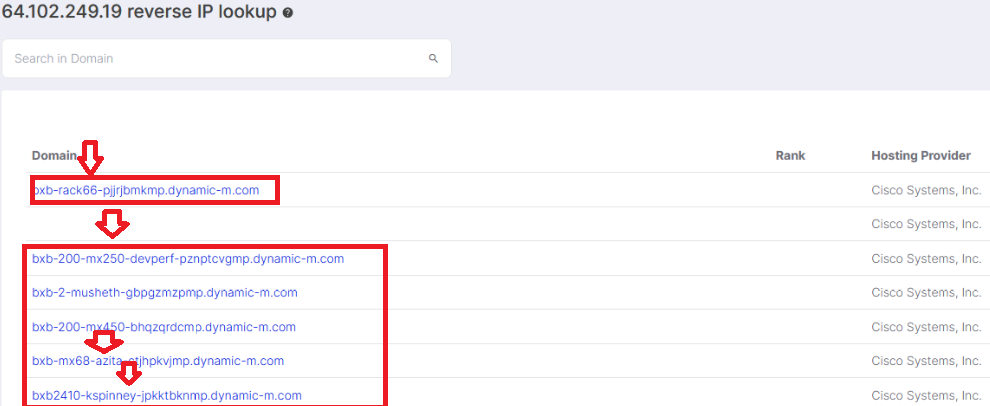
In this example, we have identified a device, a potential location, and a USERNAME. Further investigation of this IP revealed it to be publicly allocated to CISCO SYSTEMS.
Again, crawling through a well known service and searching historical data revealed this to likely be a deployment lab or staging area for CISCO MERAKI engineers. Searching public sources, we identified this user as KEITH SPINNEY, Engineering Technical Leader:
From this, we can accurately identify this lab as a staging area for cisco engineers, identified possible usernames for the MERAKI dashboard, can identify security / products in place, and identify potential areas of IP theft or targets for crafting of exploits against future releases:
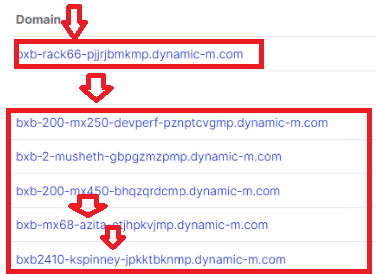
A repeated / templated deployment is tracked. The integrator or deployers has uploaded or deployed multiple revisions of this configuration here and elsewhere. Through tracking of their activities and historical DNS information dynamically updated, tracking of specific vulnerable configurations, standard & development deployments, and usernames or habits easily discovered.
GEOVISION DIPMAP.COM & GVDIP.COM DYNAMIC DNS ZONES – MAPPING AND EXPLOITING AT SCALE
The GEOVISION device automatically provisions dynamic DNS through hosted services outside of the US. Additionally, the device supports “find anywhere” functionality, enabling a user to install the device on a network with or without supporting DNS infrastructure or traditional IT assets in place.
The details of these services, and many others used by similar device vendors, are available via OSINT. The vendor has publicly published specific zones which carry particularly vulnerable devices or aged hardware no longer being maintained or lacking updates.
Using 0-day exploits we have created, it is possible to pivot through these zones, similar to the MIRAI botnet, and quickly spin up a DDoS attack platform.
Changeover Notice for GV-DDNS Service – Transfer from ‘dipmap.com’ to ‘gvdip.com’ (geovision.com.tw)
OSINT, Brute Force DNS Zone farming & Google Dorks quickly reveal vulnerable systems and infrastructure.
SYNOLOGY – SYNOLOGY.ME DYNAMIC DNS ZONE – MAPPING AND EXPLOITING AT SCALE
Finally, the SYNOLOGY product line is aimed at a similar market and is designed with similar considerations.
Much like the issues examined previously, the SYNOLOGY devices are capable of registering themselves via the SYNOLOGY.ME zone. Again, the number of total devices and their locations are easily scrapeable via OSINT.
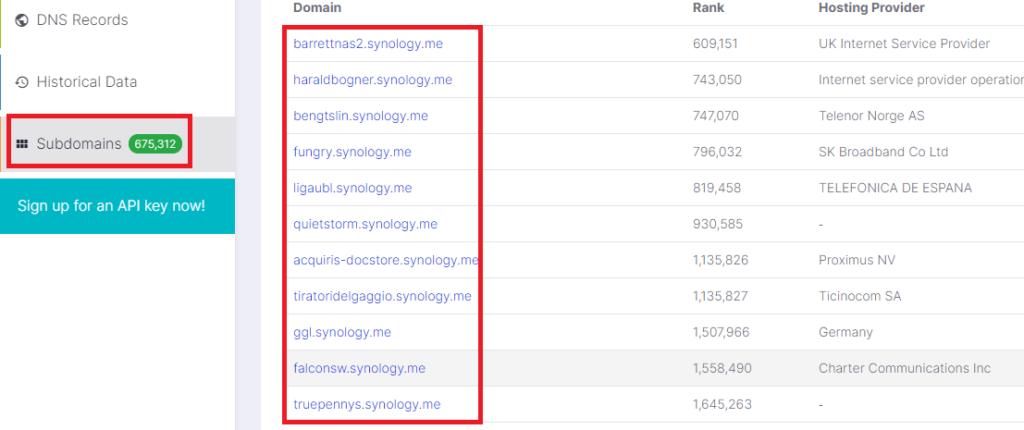
It is important to note: Synology DOES provide a warning to the user about this when implemented. It is not an adequate remediation, in our opinion.
The CYBIR Security team has performed extensive exploitation and enumeration of the SYNOLOGY class of devices.
Here, an unauthenticated API call reveals network metadata and the success or failure of web server enumeration and HOST HEADER INJECTION ATTACKS / 302 Redirects:
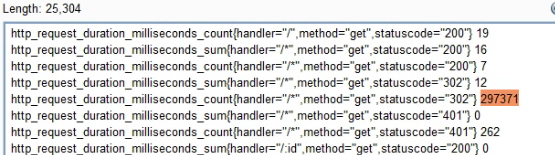
Further exploit information is being withheld at this time.
Using curated wordlists, farmed API dictionaries (such as those highlighted below), and OSINT, vulnerable devices and installs are easily discovered. (We have successfully crafted a brute forcer which does not lock target accounts out.)
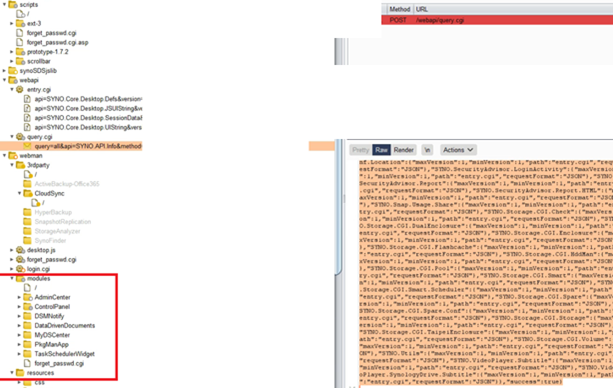
Research Attribution Proof & PoC, CVE Registrations, Relevant Theoretical Work Published
The foundational & theoretical work for these works have been developed for a number of years. I have additional private research, 0-days, and DNS or web application based RCE attacks which incorporate the theory and practice behind this entire family I have been working for years on.
The key to understanding the research is realizing that DNS is typically poorly protected, improperly secured, and an attacker controllable input / output / exploitation vector. For example, this opens the potential for malformed / malicious DNS records & attack vectors such as local exploitation or the use of DNS to deliver payloads from external or untrusted resources. Malformed DNS records * RCE can be easily triggered and the work shows how to do so with various entry points.
In our next installment, we are going to show how we can use this method and other novel attacks (Host Header Injection, API Abuses, Web Cache Farming) to provide a hyper-accurate map of internal networks, including security controls, switches, layer 2 addresses, servers, hardware, right down to LAYER 1 (the wire.)
This also serves an an entry point into turning Host Header Injections into Client-Side Code Execution vectors across multiple OS’s and platforms.
Additional proof, canaries, research, and code are currently being held private by the researcher.